Dieses sind drei der Begriffe und Themen, die heute in nahezu allen Bereichen unser Leben bestimmen. Meistens werden Arbeit und Aufgaben damit deutlich einfacher, wenn nicht sogar erst möglich.
Doch bei allem Positiven und allen Vorteilen der schönen neuen IT-Welt bringen diese Themen auch vielfältige Herausforderungen mit sich: Herausforderungen insbesondere bei den Themen Sicherheit, Schutz, Verfügbarkeit und Verlässlichkeit der IT, heute bekannt unter dem umfassenderen Begriff Cyber-Sicherheit. Die militärische Welt der Deutschen Marine und der maritime Rüstungs- und Nutzungsbereich bilden dabei keine Ausnahme.
Ausmaß der Digitalisierung
Die Schiffe und Boote der Marine sind bereits seit Jahrzehnten in weiten Teilen mit Informations- und Kommunikationstechnologie ausgestattet. Bereits die dampfgetriebenen Zerstörer Z103 wurden Ende der 1960er Jahre schmunzelnd „digitalisierte Samoware“ genannt. Erste Rechneranlagen – so nannte man IT damals noch – fand man vor allem im zentralen Führungs- und Waffeneinsatzsystem, das mit Sensoren und Waffen zu Funktionsketten verbunden war.
In den Folgejahrzehnten wuchs die Zahl der digitalen Rechner an Bord der Fregatten (F122, F123), der Schnell- und auch der Minenkampfboote ganz erheblich. Im operativen Bereich kamen Führungsinformationssysteme, im Bereich der Logistik sogenannte Fachinformationssysteme und im Bereich der Schiffstechnik Steuerungs- und Überwachungssysteme an Bord. Die operativen und logistischen Systeme wurden über Funk und zunehmend auch per Satellit an die Umwelt angebunden.
Mit der Einführung der Fregatten F124, der Korvetten und der neuen U-Boote in den frühen 2000er Jahren erreichten die schwimmenden Einheiten der Marine eine kaum noch nachvollziehbare IT-Dichte und Komplexität. Führungs- und Waffeneinsatzsysteme, Waffen, Sensoren und Navigationsbereich sind voll digitalisiert und in einem Hochleistungsnetzwerk zusammengefasst, und auch die Kommunikations- und Führungsinformationssysteme sind weitgehend im Einsatzsystem integriert.
Vor allem aber macht die umfangreiche Digitalisierung keinen Halt mehr vor ehemals bit-freien Bereichen. Mittlerweile sind nahezu alle schiffstechnischen Aggregate mit unzähligen Sensoren ausgestattet und kommen nur noch höchst selten ohne steuernde, programmierbare und überwachende Elektronik aus (sogenannte Operational Technology, OT). Zur Verdeutlichung der Situation sei erwähnt, dass die auf vielen Fregatten verwendeten Gasturbinen durch einen Steuerrechner kontrolliert werden, der einer Großrechenanlage mit entsprechender Speicherkapazität aus den 1990ern entspricht. Und auch die Ansteuerung einer vergleichsweise einfachen Axialkolbenpumpe hat die Leistungsfähigkeit eines vollständigen Arbeitsplatz-PC des Typs 80386.
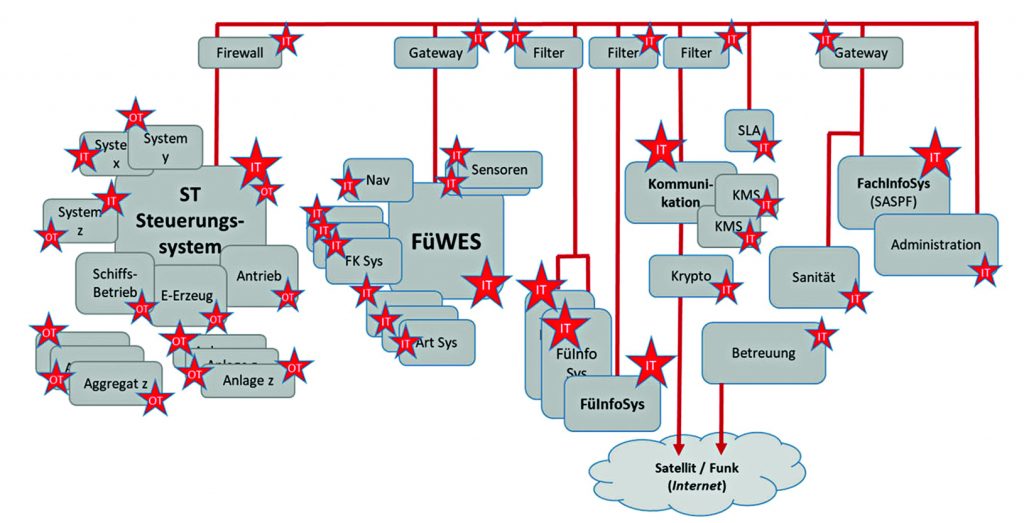
Zu den digitalisierten schiffstechnischen Anlagen kamen noch weitere IT-Systeme und Netzwerke im Bereich Logistik, Administration und zur Betreuung der Soldaten hinzu, die erstmals auch (kommerzielle) Kommunikationsverbindungen über das Internet zu ihren Gegenstellen herstellen.
Den vorläufigen Höhepunkt in der Digitalisierung und Vernetzung der Schiffe und Boote der Marine bilden die Fregatten der Klasse F125 und absehbar auch die derzeit in der Definition befindlichen neuen Mehrzweckkampfschiffe (MKS 180). Hier ist die Schiffstechnik nun vollständig mit allen anderen Systemen verbunden, zusammen in einem Netzwerk organisiert und – wenn auch gesichert – mit der Außenwelt und dem Internet verbunden.
Diese umfängliche Digitalisierung und Vernetzung ist gewollt und notwendig. Einsatz- und Wirkungsüberlegenheit funktionieren heute und künftig nur durch Informationsüberlegenheit. Und diese erfordert eine weitgehende Digitalisierung und eine umfängliche Einbindung der Führungs- und Führungsinformationssysteme in entsprechende Informationsverbünde. Gleiches gilt für Logistik, Administration und die Betreuung der Soldaten. Neu ist allerdings die Vernetzung der Schiffstechnik mit dem Ziel eines reaktionsschnellen Ressourcenmanagements, ihrer Einbindung in die landseitige Logistik und in die Instandsetzungsketten oder für eine Fernwartung der Systeme durch Vertragsunternehmen in der Heimat.
Dabei ist es vor allem diese neue Vernetzung der Schiffstechnik und der oben erwähnten Aggregate und ihrer Steuerungen, die es näher zu betrachten gilt. Die Ankunft im Netz der Netze und eine – wenn auch mittelbare – physische Anbindung an das Internet war bei der Entwicklung dieser Systeme in den 1980er und 1990er Jahren niemals vorgesehen. Seinerzeit wurden heute gängige Sicherheitsstandards (z. B. sichere Betriebssysteme, Updateverfahren, Kapselungen) insbesondere in einer umfassenden Vernetzung, wenn überhaupt, dann nur nachrangig berücksichtigt. Damit existieren nun nennenswerte schwächste Glieder und damit zum Teil erhebliche Sicherheitslücken im Gesamtsystem.
Bedrohung
Dieses wäre kein Problem, doch die IT-Welt, der Cyber-Raum und das Internet sind keineswegs sicher. Terroristen, Aktivisten, aber auch staatliche Akteure haben diese Bereiche als primäres Ziel für ihre Zwecke erkannt und machen die Nutzung streitig.

So finden Konflikte schon heute und erst recht künftig mit hoher Wahrscheinlichkeit nicht mehr ohne eine Cyber-Begleitung (von Hackerangriffen bis zu Informationskampagnen) statt. Und diese Konflikte werden absehbar weit im Vorfeld einer offensichtlichen, herkömmlichen Konfrontation auf dem neuen Schlachtfeld Cyber-Raum/Internet entschieden werden.
Das Internet ist dabei das offensichtlichste Einfallstor für solche Angriffe. Ziel sind dabei alle Netzwerke, die mit dem Internet verbunden sind. Mit jeder noch so gut gesicherten Verbindung zum Netz existiert auch ein Sicherheitsrisiko. Und es gibt heute kein Netzwerk, in das sich nicht irgendwie eindringen lässt – maßgeblich ist das Aufwand-Nutzen-Verhältnis. Ist ein Angreifer aber in ein Netzwerk eines Schiffes eingedrungen, ist der Übergang in andere Teile meist ebenfalls realisierbar und beispielsweise eine Außerkraftsetzung oder Manipulation der Schiffsantriebsanlage, der E-Versorgung oder auch der Klimaanlage eines Schiffes möglich.
Daneben ist auch denkbar, externe Informationsquellen, die Verbindungen zu diesen oder auch die zugehörigen IT-Systeme selbst zu stören oder zu manipulieren. Ein Beispiel ist das Global Positioning System, mit dem nicht nur Standorte ermittelt, sondern auch Sensoren und Waffen mit Informationen versorgt werden. So ist es heute ohne großen Aufwand möglich, über manipulierte GPS-Signale Schiffe, Drohnen oder Flugkörper auf Abwege zu bringen oder Unfälle zwischen zivilen und militärischen Einheiten zu provozieren.
Eine zunehmende Bedrohung bilden aber auch die modernen logistischen Systeme. So lassen sich Schadteile über die Versorgungskette oder auch Schadcodes über Fernwartungsprozesse unbemerkt an Bord bringen, wenn eine eingehende Prüfung unterbleibt. Hier bleibt der Mensch in der Verantwortung, die neuen Methoden sicher zu gestalten.
Genau dieser ist aber das wahrscheinlich größte Einfallstor. Einerseits agiert der Mensch dabei als Innentäter, der zielgerichtet das System von innen angreift – ob gewollt oder unfreiwillig gesteuert durch Ausnutzung seiner Schwachstellen (Social Engineering). Andererseits ist es vor allem der unbedarfte, unzureichend ausgebildete und sensibilisierte Nutzer, der durch seinen fahrlässigen Umgang mit der komplexen IT und den Netzwerken ein zunehmendes Sicherheitsrisiko darstellt und viele Angriffe erst möglich macht.
Dieses ist nur eine Auswahl an Angriffsmöglichkeiten auf dem neuen Schlachtfeld, auf das sich die Marine mit ihren digitalisierten, automatisierten und vollvernetzten Einheiten begeben hat. Sie sind vielfältig, eine dauerhafte sowie stark zunehmende Bedrohung und kaum zu verhindern. Anpassen könnte man die Angriffsfläche. Die Cyber-Bedrohung würde tatsächlich kaum noch eine Rolle spielen, wenn man auf moderne IT und Vernetzung verzichtet und zu analoger Technik, im Extremfall zu Bleistift und Papier, zurückkehrt (Back to the Roots). Doch aus guten Gründen ist ein Verzicht auf leistungsfähige IT und auf Vernetzung und Automatisierung heute keine Option.
Die heutige Welt verlangt hochtechnisierte, hocheffiziente Streitkräfte, schnellste Reaktionszeiten und maximalen Überblick, um auch in einem traditionellen und hochintensiven Kampf zu bestehen.
Doch zusätzlich ist auch ein modernes Cyber-Szenario, gegebenenfalls vor einem offenen Konflikt, wirkungsvoll zu bewältigen. Dafür ist es notwendig, auch der Cyber-Bedrohung und den aus Vollvernetzung und Automatisierung resultierenden Risiken entsprechend zu begegnen.
Hierzu wiederum sind die umfangreich und vielfältig an Bord der Schiffe und Boote eingesetzten IT-/OT-Systeme und die diversen Netzwerke deutlich abgesicherter und verlässlicher zu gestalten, als Grundlage für die Missionserfüllung, aber auch für die Sicherheit und den Schutz von Mensch und Material.
Risiko
War die Rede bisher von der allgemeinen Bedrohung, gilt es vor einer Aussage zu Lösungsansätzen zunächst abzuschätzen, wie groß das konkrete Risiko und der abgeleitete Handlungsbedarf für die Deutsche Marine und auch für die maritime Beschaffungsseite wirklich ist.
Spricht man von konkreten Risiken eines Cyber-Angriffs, sind neben der bisher betrachteten Bedrohung auch die Aspekte der Eintrittswahrscheinlichkeit und der nachfolgenden Auswirkungen mit zu berücksichtigen:
Risiko = Bedrohung x Eintrittswahrscheinlichkeit x Auswirkung
Der Umfang der grundsätzlichen Bedrohungen aus dem Cyber-Raum, die neben die klassischen Bedrohungen kinetischer Art getreten sind, wurde oben dargestellt.
Durch die Zunahme der Digitalisierung, Automation und Vernetzung ist eine breite Angriffsfläche für potenzielle Gegner im Cyber-Raum geschaffen worden. Zudem erscheinen diese Gegner angesichts von verfügbarer Hochtechnologie, Zeit und Systemressourcen eindeutig im Vorteil. Ungestört und ohne Druck können sie an jeder Stelle der IT-Landschaft der Marine eine Schwachstelle oder einen illegalen Zugang finden. Demgegenüber müssen die Wächter rund um die Uhr und überall im höchsten Maße wachsam sein und kontinuierlich die IT-Systeme verteidigen. So stellt sich in Expertenkreisen schon lange nicht mehr die Frage „Ob“ und auch nicht mehr „Wann“ ein folgenschwerer Angriff auch gegen die IT-Systeme der Marine erfolgt.
Es ist stattdessen vielmehr eine Frage der Intensität und der Auswirkungen. Dabei könnte der Schaden eines Angriffes auf die IT-Systeme an Bord durchaus bis zu einem umfänglichen Missionkill oder auch zu einem Totalverlust eines Schiffes reichen, wenn man sich die fatalen Auswirkungen der kürzlich gehäuft aufgetretenen Navigationsfehler auf Marineeinheiten im Pazifik oder vor Norwegen vor Augen führt.
In die obige Formel eingesetzt, ergibt sich also ein erhebliches konkretes Risiko für das Material, vor allem aber für die beteiligten Soldaten der Marine und daher auch ein erheblicher Handlungsbedarf.
Lösungsansätze
Zum Schutz der Schiffe und Boote gegen die klassischen Risiken werden seit Langem umfangreiche Maßnahmen der Verteidigung – von aktiven und passiven Waffensystemen bis hin zur Härtung und Erhöhung der Standkraft – eingesetzt.
Im Bereich der Cyber-Sicherheit besteht dagegen noch deutlicher Spielraum für Aufwuchs, auch wenn bereits ein Schutz vor Angriffen auf die digitalen Systeme der Marine besteht. Im Folgenden werden einige (mögliche) Handlungsfelder und Lösungsansätze vorgestellt:
Aktuell erfolgt Schutz vor allem durch organisatorische und auf klassische IT-Bedrohungen ausgerichtete Verfahren und Vorschriften (Einzelbetrachtung, isolierter Schutz durch Firewalls, Datendioden oder Virenscanner).
Erst vergleichsweise wenige Maßnahmen widmen sich der Konfiguration und Härtung gegen aktuelle Bedrohungen aus dem Cyber-Raum, um eine Verbesserung der grundsätzlichen Widerstandsfähigkeit, der Resilienz der IT-Systeme gegen Cyber-Angriffe zu erreichen.
Auch bedarf es insbesondere bei einem hochkomplexen System Schiff neben der Härtung der Einzelsysteme einer übergreifenden und ausgewogenen Betrachtung der Resilienz für alle IT-/OT-Systeme sowie die dazwischenliegenden Netzwerke im konkreten Zusammenhang einer entsprechenden Sicherheitsarchitektur.
Eine solche Gesamtsystembetrachtung ist prinzipiell durch den vom Bundesamt für Sicherheit in der Informationstechnik (BSI) erstellten IT-Grundschutzkatalog vorgesehen und vorgegeben, denn er ist verpflichtende Grundlage für die Umsetzung der IT-Sicherheit in der Bundeswehr und berücksichtigt mit einem Baustein „Schiff“ sogar spezielle Belange der Marine.
Allerdings ist Cyber-Sicherheit kein starrer Zustand, sondern ein hochdynamisches Feld. Ein eben noch sicheres und gut geschütztes System kann im nächsten Moment, mit der nächsten Entwicklungsstufe der Technik oder einer neu entdeckten Sicherheitslücke schon höchst bedroht sein. Erforderlich ist also eine ständige Aktualisierung der Sicherheitsmaßnahmen, ein agiles Update-Management und eine verlässliche sowie akkurate Administration für alle Systeme.
Zu einer umfänglichen Cyber-Sicherheitsbetrachtung gehört auch eine deutlich stärkere Berücksichtigung der Dimension Mensch und die kontinuierliche Erziehung und Ausbildung der Nutzer, um u. a. sowohl für aktuelle Sicherheitserfordernisse zu sensibilisieren, als auch die sogenannte Cyber-Hygiene sicherzustellen.
Diese umfangreichen und aufwendig umzusetzenden Forderungen nach Widerstandskraft mögen angesichts der oben erwähnten Unausweichlichkeit eines Cyber-Angriffes durchaus fragwürdig erscheinen. Tatsächlich wird diesem Gedanken in der üblichen Abwägung der Restrisiken Rechnung getragen: Nur noch im Einzelfall und bei besonders zu schützenden Objekten wird auf die absolute Verhinderung eines erfolgreichen Angriffs abgezielt, auch wegen der damit verbundenen erheblichen Nutzungseinschränkungen. Und weil man derartige Angriffe letztlich nicht völlig sicher verhindern kann oder will, liegt der Fokus der Anstrengungen heute eher auf dem Kampf gegen die Konsequenzen eines Cyber-Angriffes, auf der Minimierung seiner Auswirkungen und der möglichst schnellen Wiederherstellung der Einsatzbereitschaft.
Dieses ist gut vergleichbar mit der Art, wie die schiffstechnische Schadenabwehr auf Feuer oder Wassereinbrüche reagiert. Aus diesem Grund wird auch bei Cyber-Angriffen zunehmend von der Notwendigkeit einer Cyber-Schadenabwehr gesprochen.
Allerdings benötigt man auch für diesen Ansatz eine grundsätzliche Cyber-Resilienz, Härtung und Standkraft des Gesamtsystems als notwendige Voraussetzung für darauf aufsetzende Abwehrmaßnahmen.
Zu dieser Vorbereitung gehört auch ein umfassendes Lagebild, in das ebenfalls die äußere Cyber-Bedrohungslage (Intel) einfließen muss. Maßgeblich für eine frühe und schnelle Erkennung tatsächlicher Angriffe ist jedoch ein leistungsfähiges Gesamtsystem-Monitoring für alle IT-/OT-Systeme und Netzwerke an Bord. Eine effiziente Reaktion, also die Eindämmung, die Isolierung und maximale Kompensation eines Angriffs erfordert agile, proaktive und lernfähige Verfahren z. B. auf Basis Künstlicher Intelligenz. Neben leistungsfähiger Hard- und Software, die bereits auf dem Markt verfügbar ist, sind vor allem personelle Aspekte zur Unterstützung dieser Aufgabe zu betrachten. Dabei ist zu berücksichtigen, dass ein Schiff oder Boot selbst autark und unabhängig von einer heute existierenden Landunterstützung zu agieren hat, welche im Zweifel nicht mehr erreichbar sein wird. Eine personelle Komponente an Bord ist in der Lage, einerseits die Systeme sicher zu konfigurieren und das oben erwähnte umfassende Monitoring durchzuführen und andererseits die Reaktionen auf Angriffe in all ihren Facetten zeitgerecht und hochprofessionell (IT-unterstützt) zu steuern und umzusetzen, um die Systeme schnellstmöglich wieder online zu bringen.
Angesichts der mehrfach erwähnten Unvermeidbarkeit von Angriffen und der trotz aller Maßnahmen immer noch hochkomplexen Herausforderung der Erkennung und Kompensation von erfolgreichen Angriffen sollte ergänzend auch über alternative Vorkehrungen nachdacht werden, die eine Nutzung und Missionserfüllung unserer Schiffe trotz (und während) eines Cyber-Angriffes zumindest eingeschränkt erlauben.
Eine entsprechende Standkraft ist somit nicht nur für mechanische und elektrische Anlagen, sondern auch für die digitalen Systeme an Bord und auch für die IT in einsatzrelevanten technischen Anlagen erforderlich. IT sollte in kritischen Bereichen gekapselt und redundant ausgelegt sein. Darüber hinaus sollte im Sinne des Back to the Roots auch für ausgewählte Anlagen eine IT-unabhängige Bedienbarkeit abseits der komplexen Automatisierung angedacht werden. Maßnahmen zur Standkrafterhöhung und Notverfahren könnten dementsprechend nicht programmierbare und damit nicht manipulierbare IT-Hardware beinhalten und so einen nicht veränderbaren Grundbetrieb sichern und eine ständige Basiskontrolle über alle kritischen Anlagen ermöglichen.
Hier sind sicherlich neue, unkonventionelle Lösungen ebenso wie einfache, verlässliche Ansätze gefragt.
Fazit
Zusammenfassend lässt sich feststellen, dass Herstellung und Erhaltung der Cyber-Sicherheit eine höchst komplexe und aufwendige Aufgabe darstellen; dieses gilt auch für die Deutsche Marine und die zugehörigen Beschaffungsbereiche des Bundesamtes für Ausrüstung, Informationstechnik und Nutzung der Bundeswehr (BAAINBw). Doch es besteht akuter Handlungsbedarf. Unternehmerisch betrachtet würde der aktuelle Weg (ohne eine Berücksichtigung dieses Handlungsbedarfes) über kurz oder lang in einen Konkurs führen. Und aus militärisch-operativer Sicht kann es nicht das Ziel sein, bereits vor oder zu Beginn einer künftigen Konfrontation im Cyber-Aus zu enden und sicherlich auch nicht, erhebliche Gefährdungen der Besatzungen billigend in Kauf nehmen.
Angesichts des Umfangs und der Bedeutung des Themas sind Alleingänge nicht zielführend, vielmehr ist dieses Thema gemeinschaftlich und synergetisch im Verbund zwischen Marine, Beschaffungsseite und Industrie anzugehen, um gemeinsame Antworten zu finden. Auch erscheint die Intensivierung der internationalen Zusammenarbeit lohnenswert. Andere Bündnismarinen erproben bereits Systeme, welche auch für die Deutsche Marine von Interesse sein dürften. Dazu gehört sicherlich auch das Vorantreiben der dargestellten Themen BSI-Grundschutz, umfassende Cyber-Resilienz, Cyber-Schadenabwehr, vor allem aber Standkraft.
In einem ersten Schritt wäre das Thema an sich als wesentliches Handlungsfeld wahrzunehmen.
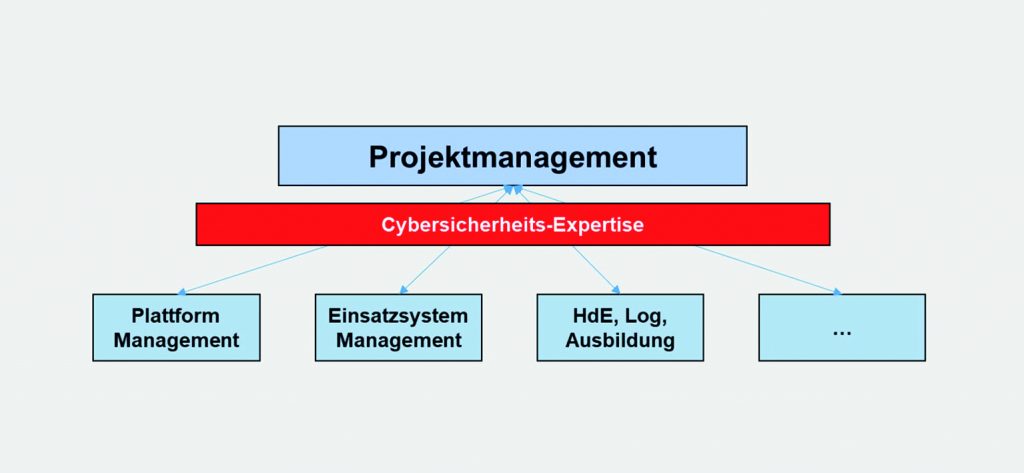
Als Teil davon sollte in anstehenden Projekten den neuen Risiken dadurch Rechnung getragen werden, dass beispielsweise ein Management eingerichtet wird, welches sich den vorgestellten Cyber-Risiken für das Projekt durch zeit- und anforderungsgemäße Wahrnehmung des Themas stellt und schrittweise unsere hochtechnisierten Marineeinheiten mit der dringend benötigten Cyber-Sicherheit und IT-Standkraft versieht.
Autoren: Leitender Technischer Regierungdirektor, Dipl. Ing. Marco Bork ist Gruppenleiter Marineführungssysteme im BAAINBw, Fregattenkapitän Jan-Peter Giesecke ist Leiter Lehre und Kommandeur Lehrgruppe Ausbildung an der Marinetechnikschule in Parow.
